20+ network diagram security
The steps in the Vulnerability Management Life Cycle are described below. To store data with a shape click View Task Panes Shape DataIn the Shape Data window type the IP address network name and other data that you want to store.

Smart Tech Ppt Template Small Pack 180093 Presentation Templates Design Bundles Smart Technologies Powerpoint Templates Powerpoint
Add labels and data.

. There are many types of computer networks including the following. This layer is also known as Internet layer. The computers are geographically close together that is in the same building.
As organizations adopt Microsoft 365 some network services and data are partly or completely migrated to the cloud. By movement of data we generally mean routing of data over the network. Explore 20 APIs.
A network is defined as a group of two or more computer systems linked together. A fishbone diagram also called a cause and effect diagram or Ishikawa diagram is a visualization tool for categorizing the potential causes of a problem in order to identify its root causes. By default deployed security admin rules arent applied on virtual networks with services that use network intent policies such as SQL managed instance service.
A network intent policy is applied to some network services to ensure the network traffic is working as needed for these services. A bow-tie diagram is a type of diagram used to model and visualize risk management and preparednessThe diagram visualizes an event with its perceived threats consequences damage mitigation measures and preventive measures. Gliffy is a fantastic drawing tool which helps you create multiple types of a diagram like Flow Chart Org Chart Venn Diagram Wireframe Mindmap Network design etc.
300 in free credits and 20 free products. The main protocol used at this layer is IP. The user interface is similar to Drawio.
The Position button on the Home tab in the Arrange group helps you evenly space shapes or change the orientation of a shape or shapes. The goal of traditional network security is to harden the corporate network perimeter against intrusion and malicious exploits. The attributes for any entity will be listed as part of a table inside each entity shape instead of separate symbols.
Extracting VoIP calls SIP RTP Building network diagram for users and network nodes extracting. You can hold the pointer over a command to see a preview of the effect it will have before you. Google Cloud Armor security policy at network edge click to enlarge.
As for any fundamental change to network architecture this process requires a reevaluation of. IDEF1X stands for integrated definition for data modeling. The following diagram illustrates the location of global external HTTPS load balancers global external HTTPS load balancer classics the Google network and Google data centers.
To move the text drag the control handle. Some also call this type of ER diagram a Relational Schema diagram. While ICMPused by popular ping command and IGMP are also used at this.
Bow-tie diagrams often called bow-ties or bowties have been successful in assisting industries such as in engineering oil and gas. Identify security vulnerabilities on a regular automated schedule. A use case diagram is a graphic depiction of the interactions among the elements of a system.
Stay up to date. To start drawing the Visio process flow diagram we will first have to open the Visio software via Microsoft 365. The commands in this section even up the spacing between shapes without changing their alignment.
Develop a network baseline. This type of ER diagram will show entities connected to each other without relationship symbols. The computers are farther apart and are connected by telephone lines or.
However I see more shapes in color which is very handy and looks attractive. Another option for labeling equipment is to use callouts which you can add from the Insert tab. There are a plethora of network security threats that businesses should be aware of to ensure the continuous protection of their systems software and data.
Inventory all assets across the network and identify host details including operating system and open services to identify vulnerabilities. Use case diagram UML use case diagram. To add text to a network shape click the shape and type.
Network intent policies and security admin rules. The main purpose of this layer is to organize or handle the movement of data on network. Lets review what we believe to be the top 10 network security threats and solutions that you can use to protect your network from being compromised by these malicious attacks.
The main intention behind this project is to help network administrators and security researchers responsible for analyzing network traffic and identifying weaknesses. Then you will have to click on the category that mentions the process flow diagram so that you can start with your work. Follow these simple steps to create a process flow diagram in Visio.

20 Overlooked Facebook Timeline Tips You Must Know Social Media Facebook Timeline Facebook Marketing

20 Welcome Linkedin Mind Map Job Security Delivery Jobs

20 Free And Open Source Social Network Analysis Software Butler Analytics Data Visualization Course Data Visualization Data Vizualisation

World S Largest Professional Network Internet Business Analysis Iot

The Skip Gram Model Words Context Model

Simple Local Area Network Lan Berbagisolusi Ethernet Cable Local Area Network Computer Maintenance

Ieee Standards For Smartcity Technologies Infographic Smart City Learning Technology Deep Learning

Free Vector Wireless Technology Devices Isometric Icons Set Electronics Gadgets Modern Business Cards Design White Business Card Design

Pin By Sean Korzdorfer On Security Personalized Prints Custom Posters Poster Design

Best Practices For Managing Complex Product Bundles Aha Support Helpful How To Articles And Videos Knowledge Best Practice Supportive

Market Overview Slides Business Powerpoint Templates Marketing Concept Marketing
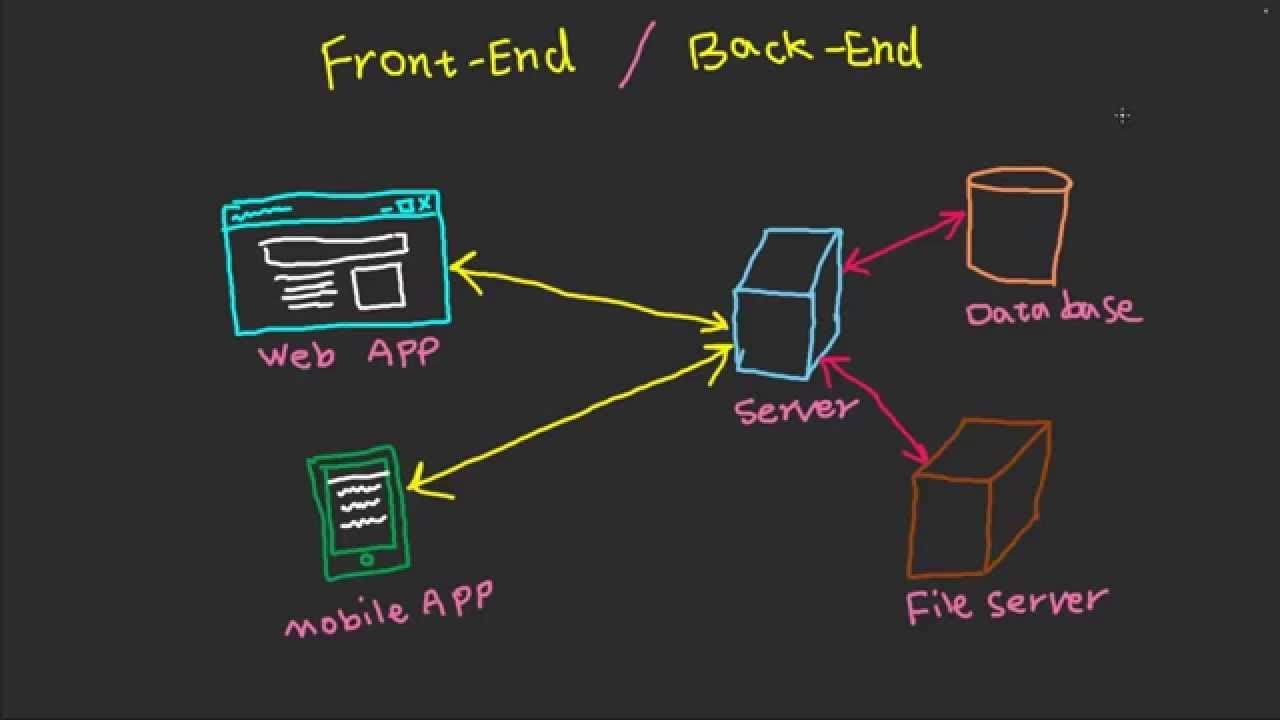
3 Frontend And Backend Fast Tech Skills Website Development Company Frontend Backend

Network Cable Ethernet Cable Ethernet Wiring

Robotic Process Automation In The Banking Industry Opteamix Banking Industry Business Accounting Software Onboarding

Next Generation Firewall Images From Palo Alto Cisco Sonicwall Computer Security Palo Alto Firewall Generation

Comprehensive Preventive Maintenance Program Involving Multiple Steps From Preparatory Activities To Conti Preventive Maintenance Work Organization How To Plan

Pin On Community Wellbeing